The Internet, or what we know as the World Wide Web, became a sensation in the late 90s and early 2000s. Since then, a lot has changed, including the discovery of its hidden and dark side. The dark web isn’t one of the safest places to navigate through.
When we speak about the dark web, we’re referring to web pages that aren’t indexed by search engines. Basically, it is a part of the internet you wouldn’t be able to find through typing on Google, Bing, or DuckDuckGo. Accessing the dark web is only possible with specialized software such as Tor Browser, and it’s not the safest place to browse.
Accessing the hidden wonders of the internet may excite some, but the danger is just one click away. Here are a few things to consider when navigating the dark web
- The Darknet is Filled With Supermarket
- New Dark Web Services Are Available
- Law Enforcement Are Watching
- Ransomware and Stealer Malware
- Using the Darknet Doesn’t Make You Anonymous
- Use the DarkWeb to Access More DarkWeb
- Some sites are by invitation only
- Dark web usage is increasing
- The dark web isn’t all that bad
- Replicates the Corporate World
- How do organizations combat the threats from the dark web?
The Darknet is Filled With Supermarket
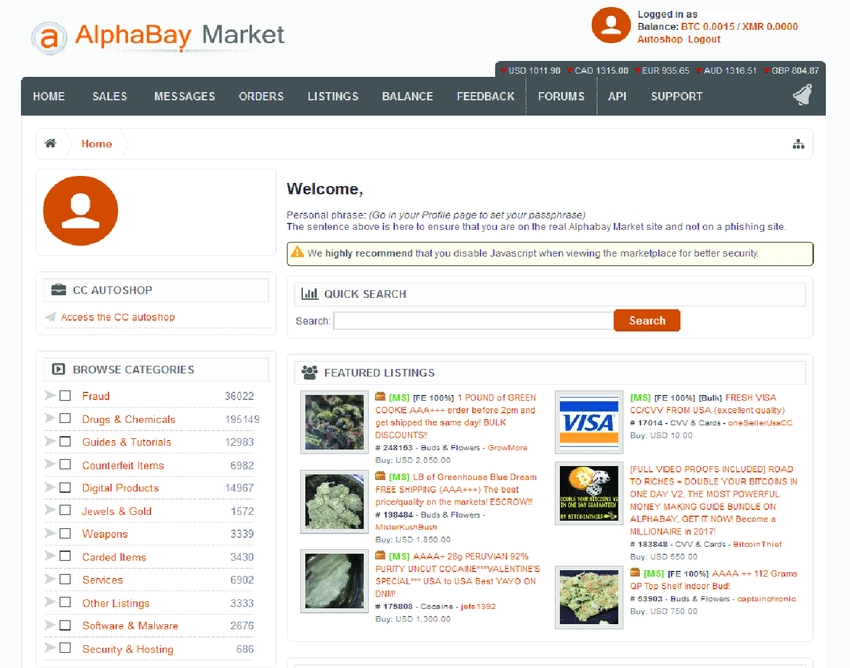
Think of it, and we guarantee you it will be available on the dark web. Just about everything can be found on the dark web including drugs, Netflix accounts, exploits, stolen credentials, weapons, poisons, and access tools. We call these places Darknet Markets
Stolen credentials and data are the most commonly sold commodities available through the dark web. Social security numbers, addresses, and credit card information are particularly popular. Most people don’t even know that their information has been exploited and is up for purchase on the dark web.
In fact, according to a recent study, there are over 24 billion stolen credentials circulating on the dark web. Since June 2022 and May 2023, over 100,000 stolen Open AI ChatGPT credentials have made their way to the dark web. Username and password credentials offered for sale on the dark web have increased by 65% since 2020, and they’re cheap!
Currently, the going rate for stolen credit card information goes between $70 to $110, depending on the account’s balance. Hackers purchase these credentials to gain unauthorized access to business databases.
It’s important to note that many of these markets tend to grab their user’s money and run away with it eventually; Which is why you need to be careful how you pick your dark web market.
New Dark Web Services Are Available
As the number of users on the dark web increases, the demand for cybercrime services increases. The number of cybercrime services is expanding on the dark web, this includes botnets, easy-to-deploy commodities, and exploits to access like Active Directory.
Botnets are extremely popular on the dark web, and the demand for them has led to the creation of a botnet underground market. These large networks of compromised computers can be repurposed across different types of attack vectors and are used for a variety of malicious cyber activities.
Some botnets are designed to steal data, login credentials, and financial information which can then be sold on the dark web. In recent months, Monero’s Community Crowdfunding System wallet is believed to have possibly been breached with the help of a botnet. That being said, not all of these services are safe to use. Using the darknet doesn’t make you anonymous right away.
Law Enforcement Are Watching
Bad actors on the dark web sell items in exchange for cryptocurrencies to remain anonymous. The distribution of narcotics, the sale of child pornography, and stolen credentials all carry a heavy sentence for criminals if they’re caught.
Selling and purchasing prohibited items or hiring the services of a mystery hitman on the dark web are proving to be ineffective. The dark web isn’t as entirely anonymous as it may seem. Law enforcement agencies from various countries have begun to turn their attention to the dark side of the internet in an attempt to crack down on illegal activities.
Agents act as buyers and purchase products from various dark web vendors while successfully gathering information through the operation. Officers infiltrate groups and wait for members to accidentally post their email addresses to be identified.
Sometimes Law Enforcement even create fake websites to capture information on victims. We call these Honeypots. They’re designed to attract darknet users and watch their activity on the darknet. By observing how users interact with the honeypot, law enforcement can gain valuable insights into how cybercriminals use the darknet. Sometimes even bagging a few arrests along the way.
One of the biggest challenges faced by law enforcement in bringing down these groups is that they rotate their infrastructure. Criminals use multiple servers across the dark web, leaving police to chase after each server.
If one server is taken down by police law, there’s another one that will automatically replace it. To combat this, law enforcement agencies actively police the dark web using specialized techniques.
The Australian Federal Police have taken the fight to the dark web with new policing powers such as network activity and data disruption warrants. Police target the sale of stolen personal data, ransomware, and cybercrime tools.
The aim of the operation is to identify, disrupt, and arrest criminals through a partnership with international law enforcement partnerships. Joint operations across international borders have led to successful convictions in Australia.
In recent months, law enforcement agencies have shut down several dark web marketplaces. The most significant scalp is Genesis Market, with over 500,000 users and 2,400 sellers. The operation saw seventeen countries combine in a multinational crackdown. The marketplace hosted around 80 million stolen credentials and fingerprints.
Ransomware and Stealer Malware
The dark web is no longer a small and confined space of the internet, cybercriminals are always one step ahead of defenders. Bad actors are diversifying the internet, and there is an increasing interest in the use of ransomware.
Groups like Snatch Ransomware use Google ads to trick individuals into installing malware onto their devices. Once installed, the group’s malware breaches a company’s database and extracts information.

Cybercriminals use the stolen data to demand ransom money from companies. If the ransom demands aren’t met, the information is then leaked all over the dark web. Leaked data on the dark web creates a doorway for criminals to find staff and customer emails. The threat of causing harm to the reputation of an organization increases the likelihood that they will pay the ransom.
Additionally, stealer logs with access to corporate networks are some of the most popular vectors used for data breaches and ransomware attacks. Infostealer variants like Raccoon, RedLine, Titan, and Vidar infect computers and extract a browser fingerprint, which contains all the saved passwords in a browser.
Using the Darknet Doesn’t Make You Anonymous
While the Darknet does provide some anonymity, it is not foolproof. There are a number of ways that users can be tracked, including:
- Exit nodes: Tor, the most popular software for accessing the Darknet, relies on a network of relays called nodes. These nodes route your traffic through a series of other nodes before it reaches its destination. However, if an exit node is compromised, it is possible for your traffic to be monitored.
- Browser vulnerabilities: Browsers can contain vulnerabilities that can be exploited to track users. For example, a vulnerability in the Tor browser was once used to track users for over a year.
- Malicious websites: Malicious websites on the Darknet can be used to track users. For example, a website may ask you to download a file that contains malware. This malware could then be used to track your activity on the Darknet.
As a result of these risks, it is important to take precautions when using the Darknet. These precautions include:
- Using a VPN: A VPN can encrypt your traffic and make it more difficult for your ISP to track your activity.
- Using a secure browser: Tor is a good choice for accessing the Darknet, but it is important to keep it up to date and to be aware of the risks associated with using exit nodes.
- Being careful about what you download: Only download files from trusted sources and scan them for malware before opening them.
- Being aware of your surroundings: Be careful about what you say and do on the Darknet, and be aware that you may be under surveillance.
- Changing Your Usernames and Passwords: This is essential to seperate your IRL identity to online identities
Theres more to this, so I suggest you check out our article on OpSec (Operations Security) for Darknet Usage
Use the DarkWeb to Access More DarkWeb
There is more than just one dark web available; any network that is undetected by internet search engines and restricts access to it can be considered the dark web. You can purchase technical tools and information through the dark web to set up an additional dark web.
To find Darknet websites, you can use livedarknet.com or Dark.Fail. These are solid and trusted sources that will ensure you’re not being scammed along the way.
Some sites are by invitation only
An entire ecosystem on the dark web is dedicated to the sale of vulnerabilities and exploits against corporate systems, some of them by invitation only. Cybercriminals are some of the brightest minds out there, these groups go to dark web marketplaces and look for vulnerabilities in a system.
When they find these vulnerabilities, they pay a fee for an exploit that works against the vulnerability. There is a great demand for these services, some of which are provided by organized criminal syndicates on the dark web.
The orchestrators behind an attack are not always directly involved in accessing an organization’s network. Bad actors frequently pay someone else to do their dirty work, because that person paid for a vulnerability on the dark web.
Most of the bad actors that offer these services can only be accessed through invite-only forums. Gaining access can only be achieved through a link or invitation from the owner of the domain.
Invitation-only forums are designed to protect the exclusivity and security of authorized members. This makes it impossible for corporate companies and individuals to track whether they’ve experienced a data breach.
Knowing the right people or paying for access to the forum is a common way to gain access.
Trust is crucial for dark web marketplaces, after all, if the negotiation doesn’t go to plan you can’t report it to the police. Law enforcement officers have realized the importance of a trusting relationship with members of invite-only groups, to gain access.
Dark web usage is increasing
Approximately 2.7 million people access the dark web on a daily basis, this number has increased by 200,000 in the period of a year. The adoption of Bitcoin and its increase in value sparked a rise in traders on the dark web.
Many people on the dark web trade cryptocurrencies through their e-wallets. Buyers and sellers can now easily trade illegal goods and services through the dark web. However, the number of users isn’t the only thing that has increased, so has the number of relays.
There are a number of well-known forums that offer bartering, selling, exploit auctioning, and vulnerability. These websites also offer hacking tips and act as vectors for recruitment efforts by cybercriminals and ransomware groups.
New dark web domains are popping up online all the time. In most cases, a new domain is just the rebranding of older ransomware groups. When law enforcement shuts down one domain, another will arise within a few days.
Silk Road, a former dark web marketplace, was shut down by the Federal Bureau of Investigation and Homeland Security in 2013. A month later, Silk Road 2.0 was up and running, however, a year later authorities seized the replacement website.
The dark web isn’t all that bad
The darknet was initially created for people to anonymously communicate online and share files. To this day, it isn’t illegal for users to access the dark web, although the majority of transactions that occur on it are prohibited.
A legitimate purpose for anonymizing tools like Tor Browser still exists. In countries where governmental surveillance is used to monitor the press. The dark web is a platform that allows for anonymous communication which circumvents government censorship.
The problem with using anonymizing tools is that there is no censorship. Bad actors and cybercriminals have free reign to do as they please without being detected on dark web marketplaces.
Replicates the Corporate World
The dark web is slowly beginning to replicate the corporate world in various areas such as recruitment, hacking, and it’s technological advancements. To imitate the corporate world, cybercriminals create replicas of websites, banking applications, mobile applications, and social media accounts of companies to appear original.
Users who download or use a replicated site and submit their password or credentials are hacked. Cybercriminals make use of manipulated information and it negatively impacts the company’s stock price.
Additionally, dark web forums are implementing stricter access control measures to counter-attack against the increase of law enforcement activity. New users who wish to join forums are scrutinized by administrators. Groups now require new users to provide references and verification tokens.
Other dark web forums require new users to pay a significant deposit in cryptocurrency, before being accepted.
How do organizations combat the threats from the dark web?
As companies begin to store their information online, the threat of a cyber attack increases.
The dark web is a hacker’s go-to platform for anonymously selling stolen data. Thankfully, there are several tools and services that are capable of detecting the dark web for organizational threats.
Organizations need to be proactive when it comes to cybersecurity. The dark web is constantly changing and requires employees to make continual updates with regular assessments.
A dark web monitoring service is one of the ways corporations and individuals can search for information on the dark web. A monitoring service will find compromised or leaked data such as passwords, credentials, and other private information circulating amongst criminals on the dark web.
An effective dark web monitoring system will provide broad visibility without taking on the risk of entering the dark web. Monitoring services prevent administrators from being exposed to malware and security threats on the dark web.
There are various types of monitoring services available, some are fully automated, and others use AI intelligence for accurate readings. Unfortunately, monitoring services aren’t able to remove any stolen information from the dark web or stop your information from being used.
The reality of the situation is that companies are more likely to be the victim of a phishing scam or ransomware attack from clicking on malicious web links. However, the knowledge of compromised, leaked data allows companies to update their systems and avoid any further data breaches.
Conclusion
The darknet is a dangerous place, but it’s important to remember that it’s not all bad. There are legitimate purposes for using anonymizing tools like Tor Browser, and I2P can provide anonymous communication that circumvents government censorship. By taking these precautions, you can help to keep yourself and your organization safe from the dangers of the dark web.

Hey there, I’m a dark web geek who’s been around for the last 8 years. More precisely, I’m livedarknet’s senior content writer who’s been writing about darknet marketplaces, tutorials, and cybersecurity stuff for educational purposes.

